Are attackers who want to attack computers a constant threat in today’s digital landscape? This article delves into the motivations, tools, and techniques employed by attackers targeting computer systems, providing valuable insights for safeguarding against cyber threats.
From hackers seeking personal gain to nation-states engaging in cyber warfare, the landscape of attackers is diverse. Understanding their strategies and tactics is crucial for implementing effective security measures.
Common Attacker Types

Attackers who target computers have diverse motivations and goals, ranging from financial gain to political espionage. They can be classified into several types, including:
Hackers
- Motivated by curiosity, knowledge, or reputation
- May engage in illegal activities but often driven by exploration and skill demonstration
Cybercriminals, Are attackers who want to attack computers
- Primarily motivated by financial gain
- Use sophisticated techniques to steal sensitive information, extort money, or disrupt systems
Nation-States
- Conduct attacks for strategic purposes, such as espionage, military operations, or political influence
- Possess advanced resources and capabilities
Attacker Tools and Techniques
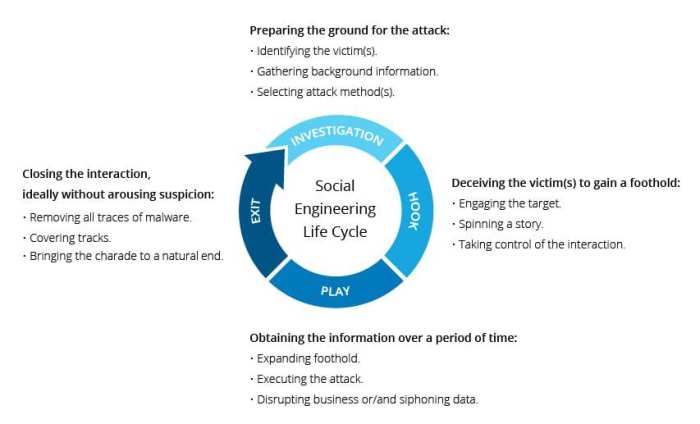
Attackers employ a wide range of tools and techniques to exploit vulnerabilities in computer systems:
Exploits
- Software that takes advantage of vulnerabilities in operating systems or applications
- Allow attackers to gain unauthorized access, escalate privileges, or execute malicious code
Phishing
- Social engineering technique that uses deceptive emails or websites
- Tricks victims into providing sensitive information or clicking malicious links
Malware
- Malicious software designed to damage or disrupt systems
- Includes viruses, worms, ransomware, and spyware
Target Systems and Vulnerabilities

Attackers target various types of computer systems, including:
Enterprise Networks
- Targeted for financial gain or espionage
- Vulnerable due to complex infrastructure and high-value data
Personal Computers
- Targeted for identity theft, data exfiltration, or financial fraud
- Vulnerable due to weak passwords and unpatched software
Mobile Devices
- Targeted for data theft, malware distribution, or financial fraud
- Vulnerable due to mobile operating system flaws and lack of user awareness
Countermeasures and Mitigation Strategies

Protecting computer systems from attacker threats requires a multi-layered approach:
Technical Measures
- Implementing firewalls to block unauthorized access
- Using intrusion detection systems to monitor network traffic for suspicious activity
- Applying patch management to fix known vulnerabilities
Administrative Measures
- Establishing strong password policies
- Implementing access control mechanisms to restrict access to sensitive data
- Conducting regular security audits to identify and address vulnerabilities
User Education
- Educating users about phishing scams and social engineering techniques
- Raising awareness about the importance of using strong passwords and patching software
- Encouraging users to report suspicious activity
FAQ Explained: Are Attackers Who Want To Attack Computers
What are the common motivations of attackers who target computers?
Attackers may be driven by financial gain, political agendas, espionage, or simply the thrill of the challenge.
How do attackers gain access to computer systems?
Attackers employ various methods, including phishing emails, malware, social engineering, and exploiting software vulnerabilities.
What are some effective countermeasures against attacker threats?
Implementing firewalls, intrusion detection systems, and patch management, along with user education and awareness, are essential for protecting systems.